Distil Networks (Now Imperva Bot Management) has detected a sophisticated gift card bot attack on its network affecting nearly 1,000 customer websites around the world and is recommending consumers check their gift card balances in case of fraud. The advanced persistent bot, named GiftGhostBot, automatically checks millions of gift card numbers to determine which have balances, and was detected on February 26, 2017 and is still attacking websites.
Gift Card Fraud: Your Gift Card in the Hands of a Bad Bot
If you have tried to check your balance on a gift card recently, you may have noticed that many retailers could not provide you with that information online. Instead, you received a message to contact customer service by phone. Why? Gift card payment processes on websites are under sustained attack from sophisticated bad bots trying to defraud people from the money loaded onto a card.
Who is GiftGhostBot Attacking?
The websites of retailers all over the globe are targets. Gift cards are typically associated with a particular company, and can be used to purchase any item sold by that company. Any website with gift card processing capability, including checking your gift card balance or replenishing funds, is a potential target.
What is GiftGhostBot Doing?
It is a card cracking or token cracking* attack. This means that fraudsters are using automation to test a rolling list of potential account numbers and requesting the balance. If the balance is provided, the bot operator knows that the account number exists and contains funds. Armed with that information, the account number can be used to purchase goods, or sold on the darkweb for a fee. For a cyber thief, the beauty of stealing money from gift cards is that it is typically anonymous and untraceable once stolen.
Bots like GiftGhostBot are used to complete this task because a human would be unable to achieve the required volume of requests. On one retail customer site, we are seeing peaks of over 4 million requests per hour, nearly ten times their normal level of traffic.
*Refer to the OWASP Automated Threats Handbook for additional information.
How does GiftGhostBot Impact Consumers?
Any consumer who has a gift card from any retailer could find the card no longer contains funds and are the victim of fraud. To date, Distil has seen this attack on almost 1,000 customer websites.
Consumers may suffer from a loss of faith in gift cards and make an irate call to the company that issued the gift card if they see their account balance disappear. Assuming the gift card is not FDIC protected or registered, if the issuing company doesn’t replenish the amount, the consumer relationship is damaged.
How does GiftGhostBot Impact Online Retailers?
Businesses have to successfully handle these dissatisfied customer calls asking for a refund to maintain their future relationship. But the business is also suffering on the front end of the attack. Requests into the website could reach millions each day and potentially inundate the servers leading to slowdowns or downtime; it amounts to an application denial of service. The data about that company’s website visitors is also seriously skewed towards fake bad bot traffic. Any data about where visitors to the website come from is seriously flawed.
How Did We See the Attack?
We protects many of the world’s largest brands from bad bots, and since February 26 our analysts noticed that companies with a gift card processing capabilities had increasing activity from malicious bots attacking that process on their websites. In several instances, over half of the traffic on the website was on the gift card page alone, indicating a very targeted attack. To understand the scale, some sites are seeing millions of requests per hour on their gift card pages, up to ten times the normal traffic.
We saw GiftGhostBot on nearly 1,000 customer websites, all of which were protected by Distil Networks (Now Imperva Bot Management).
As additional research we looked at other major retailers, not protected by Bot Management, and anecdotally saw that many have suffered intermittent problems, while some took drastic action and ceased all gift card functionality on their website for a period of time. Instead gift card holders were instructed to call a number to check their gift card balances.
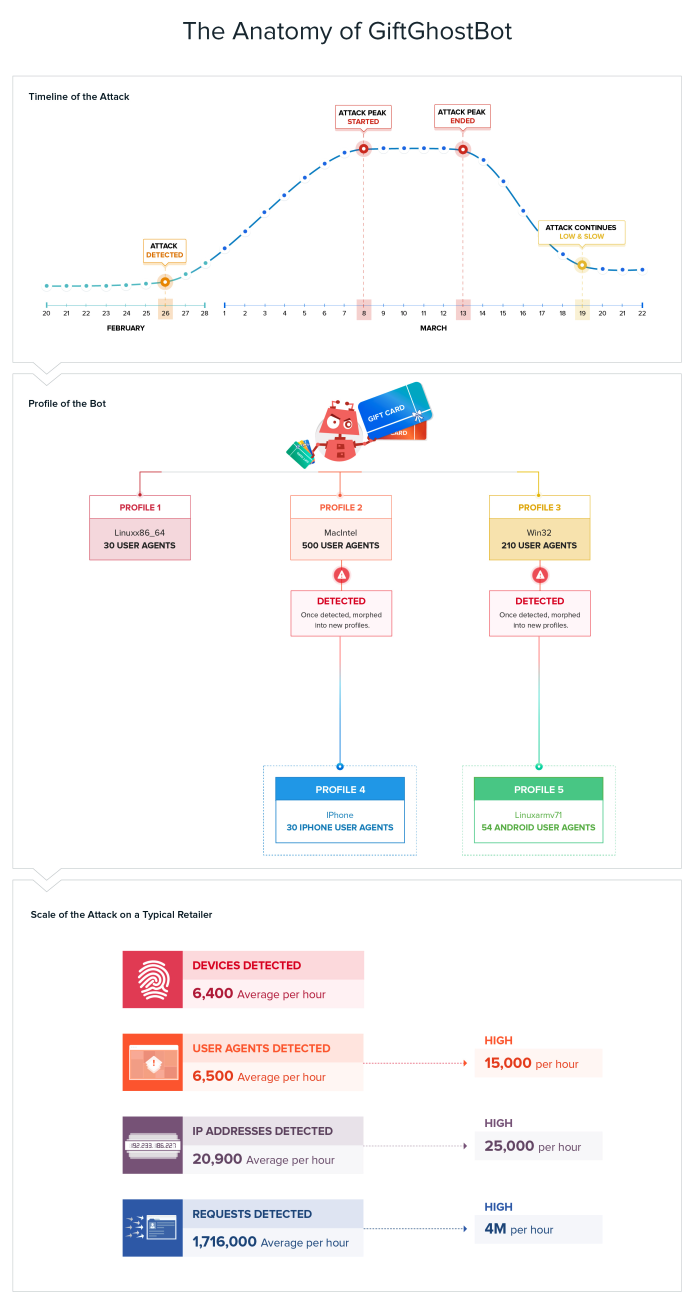
The GiftGhostBot attack was detected on February 26 but didn’t reach its peak until March 8. It sustained this peak until March 13, where it dropped off in volume, and now continues as a “low and slow” bot attack.
GiftGhostBot is an Advanced Persistent Bot
GiftGhostBot has multiple features that confirm it is an Advanced Persistent Bot (APB). First, it is lying about its identity by rotating user-agent strings. Second, it is heavily distributed across various hosting providers and data centers all over the world. Third, it is technically sophisticated when it executes JavaScript, mimicking a normal browser. Finally, it is persistent in that if it is blocked using one technique it adapts and returns using a different attack technique.
Forensic Analysis of GiftGhostBot
After forensic analysis of the attributes of the GiftGhostBot we identified five main profiles used in the attack. The first three profiles (Profiles 1, 2, and 3) indicate how the attack began and also the sophistication of the attack because collectively, GiftGhostBot cycled through over 740 user agents. Once Distil began blocking the malicious behavior of Profiles 1, 2 & 3, the bot demonstrated its persistence and proved that it was well-funded, when it disappeared only to later return, but had morphed into two very different profiles (Profile 4 & 5) and identified itself as ןPhone and Android user agents. The funding is important because the bot operator didn’t hesitate to increase the cost of the attack, even though each request would cost at least five times more by using mobile ISPs.
When we examined a typical retail customer by the numbers we see some interesting characteristics of the attack. Using our Hi-Def device fingerprinting technology, we detected on average 6,400 unique fingerprints per hour. Because the device fingerprint is more accurate than an IP address and user agent you see the average number of user agents detected were higher at 6,500 per hour, and that IP addresses were detected at an average rate of 29,000 per hour. All of these numbers indicate that the bot was distributing itself widely and trying to hide.
Are the Online Retailers at Fault?
No, it is important to understand that they are not being breached into exposing personal information. The functionality to check a balance is on their website and the bot is using that business logic to find out the information.
Is this a DDoS Attack?
No, it is a distributed attack but it is not looking to overwhelm the servers with the goal of bringing the website down. It is just using malicious automation to check which account numbers contain funds. The attack is distributed around the globe, using different IP addresses, and is hiding within different datacenters and ISPs. This is an application layer attack and while it is not designed to bring the website down, the volumes we are seeing can overwhelm some servers and potentially make parts of the website inoperable.
Recommendations for Consumers
CHECK YOUR GIFT CARD BALANCES – For consumers, we recommend you check your balance on any gift card and take a screenshot of the page showing the account balance as proof.
TREAT GIFT CARDS LIKE CASH – Don’t forget about your gift cards and leave money unused. This helps not only to prevent fraud, but also to avoid losing or forgetting the gift card.
CONTACT THE AUTHORITIES – For those in the US facing problems with cards issued by retailers, contact the Federal Trade Commission or call toll-free: 1-877-FTC-HELP. You may file a complaint with your state Attorney General (for a list of state offices, visit naag.org). For those in the UK, the Financial Ombudsman website is a good starting point, while in Ireland the ConsumerHelp website from the Competition and Consumer Protection Commission should be able to assist as well. In Europe, the European Consumer Centres Network (ECC-Net) would be a good starting point.
Recommendations for Retailers
INSERT A CAPTCHA – A best practice would be to include a CAPTCHA on the Check-your-Gift-Card-Balance page. While not effective against the most sophisticated bots, it prevents many bots.
EXAMINE YOUR WEB TRAFFIC TO KNOW IF YOU WERE TARGETED – For retailers, sophisticated bad bots constantly rotate their IP address in order to hide within normal traffic, but in order to protect the balances of gift cards around the world, we are providing the known IP addresses involved in the attack. We recommend researching these IP addresses within your logs during the period Feb 26-March 15, 2017.
| 64.187.230.180 | 45.32.198.184 | 85.114.142.229 | 192.240.195.226 |
| 64.187.230.224 | 104.238.156.175 | 35.187.193.218 | 192.240.195.235 |
| 52.14.148.78 | 45.32.141.174 | 192.184.1.191 | 192.240.195.111 |
| 52.14.41.165 | 45.63.37.51 | 192.184.1.150 | 66.187.74.7 |
| 52.14.147.249 | 45.76.65.176 | 192.184.2.20 | 66.187.74.58 |
| 54.197.1.68 | 45.63.95.80 | 192.184.1.201 | 62.32.95.126 |
| 45.57.231.243 | 45.32.66.230 | 192.171.254.205 | 173.236.63.33 |
| 23.236.209.134 | 216.10.3.211 | 69.94.25.46 | 198.134.105.14 |
| 23.236.209.91 | 216.10.7.158 | 65.18.169.117 | 104.222.130.144 |
| 23.229.9.38 | 216.10.3.182 | 192.110.164.76 | 104.222.130.212 |
| 108.61.222.44 | 64.187.237.216 | 184.164.74.234 |
RATE LIMIT REQUESTS TO GIFT CARD PAGE – Another best practice would be to put rate limits on requests to the check your balance page.
CONSIDER A BOT MITIGATION SOLUTION – Retailers should look at bot mitigation solutions like Distil that help reduce gift card fraud and also help with other bot related issues like preventing account takeovers, credit card carding, and price scraping.
Will this Prevent the Bad Bots for Good?
No, this will delay them for a period of time. Sophisticated bad bot operators are constantly changing how they attack and if your organization is a target, they will come back. Only automated solutions are successful against automated attacks.
Try Imperva for Free
Protect your business for 30 days on Imperva.

