What is Credit Card Cracking
Card cracking is a credit card fraud technique that leverages bots (software that runs automated tasks over the Internet).
Cracking is based on the idea that it is easy to obtain a credit card number, known as a Private Account Number (PAN), together with the name printed on the card. Attackers use bots to guess and confirm the additional information required to “crack” and illicitly use a credit card.
There are several ways criminals can obtain PANs:
- Buying lists of PANs on the dark web
- Through accomplices working in retail or restaurants who are exposed to credit card information
- By skimming, which means adding a device to a credit card swiper that enables unauthorized parties to read the card information and PIN
- By phishing scams, which typically involve calling the credit card owner and pretending to be an authorized party requesting their credit card details
Once a criminal obtains a PAN, they still need the following additional details to steal funds. Each of these can be guessed because they have a small number of possible combinations:
| Data to crack | Number of possible values | Ease of guessing |
| 3-digit CVV number | 1000 | Medium |
| Expiration date | 60 (expiry date is up to 5 years) |
Easy |
| Zip code | 3000 (in the USA) |
Medium |
By obtaining a list of PANs, and deploying a bot that can contact multiple websites and try different combinations of the other parameters – CVV, expiration date and ZIP – attackers can quickly “crack” a credit card and use it to steal funds from its owner.
Example Procedure for Credit Card Cracking
Here is an example of a process attackers could follow to crack credit cards at large scale.
- Obtain a list of PANs.
- Set up a bot that can attempt small purchases on a large list of payment sites. The bot should attempt a purchase on a website, submitting credit card information for a PAN, and each time guessing a different combination of CVV, expiration and ZIP code.
- Deploy the bot to operate on 30 payment sites in parallel, to avoid guessing limits.
This procedure would allow an attacker to crack a card every four seconds, and scale up the process to crack as many as 21,600 stolen credit cards per day.
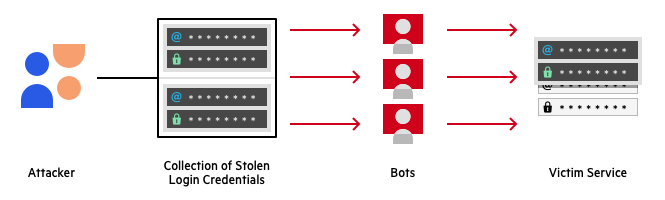
Example of credit card cracking
How to Protect Against Card Cracking Bots
The following techniques can help you safeguard your payment site against bad bots used in credit card cracking.
Device fingerprinting
Fingerprinting is done by combining the user’s browser and device to understand who or what is connecting to the service. Fraudsters or bots who are attempting credit card fraud need to make multiple attempts, and cannot change their device every time. They will need to switch browsers, clear their cache, use private or incognito mode, use virtual machines or device emulators, or use advanced fraud tools like FraudFox or MultiLogin.
Device fingerprinting can help identify browser and device parameters that remain the same between sessions, indicating the same entity is connecting again and again. Fingerprinting technologies can create a unique device, browser and cookie identifier, which, if shared by multiple logins, raises a suspicion that all those logins are part of a fraud attempt.
Browser Validation
Some malicious bots can pretend to be running a specific browser, and then cycle through user agents to avoid being detected. Browser validation involves validating that each user browser is really what it claims to be – that it has the expected JavaScript agent, is making calls in a way to be expected from that browser, and is operating in a way that is expected from human users.
Machine Learning Behavior Analysis
Real users visiting a payment website exhibit typical behavior patterns. Bots will typically behave very differently from this pattern, but in ways, you cannot always define or identify in advance. You can use behavioral analysis technology to analyze user behavior and detect anomalies – users or specific transactions that are anomalous or suspicious. This can help identify bad blots and prevent cracking attempts.
As part of behavioral analysis, try to analyze as much data as possible, including URLs accessed, site engagement metrics, mouse movements, and mobile swipe behavior.
Reputation Analysis
There are many known software bots with predictable technical and behavioral patterns or originating IPs. Having access to a database of known bot patterns can help you identify bots accessing your website. Traffic that may appear at first glance to be a real user, can be easily identified by cross-referencing it with known fingerprints of bad bots.
Progressive Challenges
When your systems suspect a user is a bot, you should have a progressive mechanism for “challenging” the user to test if they are a bot or not. Progressive testing means that you try the least intrusive method first, to minimize disruption to real users.
Here are several challenges you can use:
- Cookie challenge – transparent to a real user
- JavaScript challenge – slightly slows down user experience
- Captcha – most intrusive
Additional Security Measures
Beyond the above techniques, which allow you to directly validate if traffic originates from a real user or a bot, use the measures below to strengthen your security perimeter against cracking bots.
Multi-factor authentication
eCommerce sites can require users to sign in with something they know (for example, a password) and something they have (for example, a mobile phone). While this does not prevent cracking, it makes it more difficult for criminals to create large numbers of fake accounts, and renders it almost impossible for them to take over existing accounts.
API security
eCommerce sites often use credit card APIs, such as those offered by PayPal or Square, to facilitate transactions. These APIs can be vulnerable to attacks, such as JavaScript injection or the rerouting of data, if not incorporated with the appropriate security. To protect against many of these attacks, eCommerce sites can use a combination of Transport Layer Security (TLS) encryption and strong authentication and authorization mechanisms, like those offered by OAuth and OpenID.
Imperva Bot Management
Imperva’s Bot Management solution can protect against credit card cracking bots by using all the security measures covered above, letting you identify bad bots with minimal disruption to real user traffic:
- Device fingerprinting
- Browser validation
- Behavioral analysis
- Reputation analysis
- Progressive challenges
In addition, Imperva covers the additional security measures that complement a defensive bot strategy. It offers multi-factor authentication and API Security – ensuring only desired traffic can access your API endpoint and blocks exploits of vulnerabilities.
Beyond bot protection, Imperva provides multi-layered protection to make sure websites and applications are available, easily accessible and safe, including:
- DDoS Protection—maintain uptime in all situations. Prevent any type of DDoS attack, of any size, from preventing access to your website and network infrastructure.
- CDN—enhance website performance and reduce bandwidth costs with a CDN designed for developers. Cache static resources at the edge while accelerating APIs and dynamic websites.
- WAF—cloud-based solution permits legitimate traffic and prevents bad traffic, safeguarding applications at the edge. Gateway WAF keeps applications and APIs inside your network safe.
- Account Takeover Protection—uses an intent-based detection process to identify and defends against attempts to take over users’ accounts for malicious purposes.
- RASP—keep your applications safe from within against known and zero‑day attacks. Fast and accurate protection with no signature or learning mode.